Hackers are targeting WordPress websites — over 2 million websites compromised already!
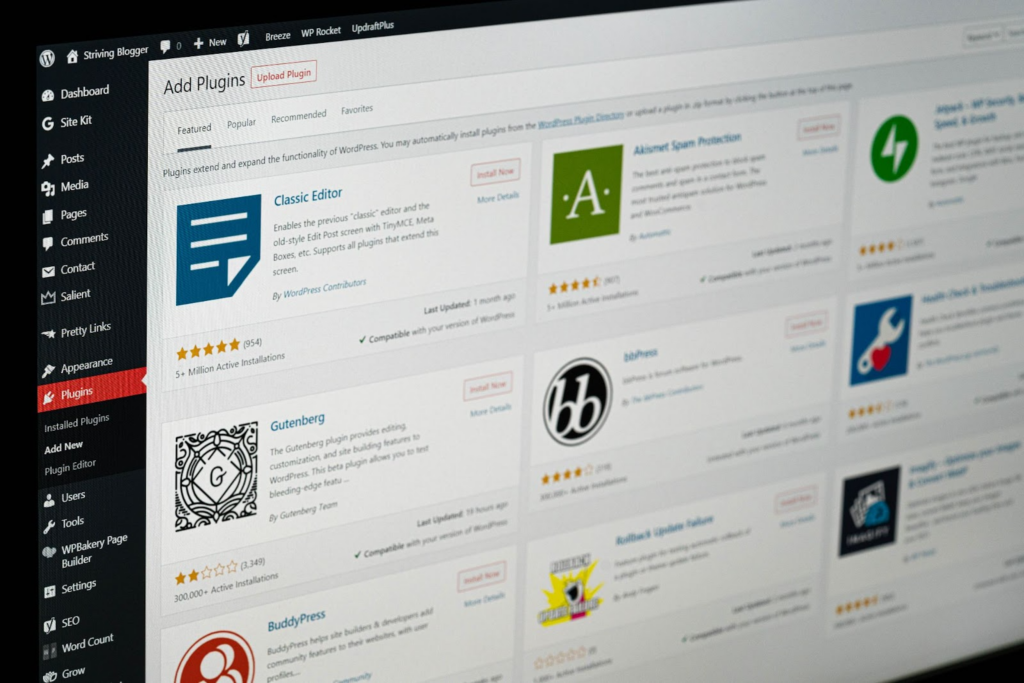
Every day, humans click on links they are not supposed to, which leads to websites being breached and hackers getting their hands on crucial content. Content that includes not only source code and script that organizations work hard to keep confidential but also other sensitive information, including but not limited to user/account details and passwords. Website owners are advised to update the respective plugin immediately and block IP addresses associated with the attacks.
WordPress websites using the Essential Addons for Elementor plugin are being targeted by hackers. Essential Addons for Elementor is a popular WordPress plugin that enhances the functionality of the Elementor page builder. Elementor is a drag-and-drop page builder plugin for WordPress that allows users to create and customize websites easily without any coding knowledge. The plugin had a critical flaw (CVE-2023-32243) that allowed attackers to reset administrator passwords and gain control of the websites. It also allows attackers to inject arbitrary executable scripts into vulnerable websites. Reflected cross-site scripting (XSS) attacks occur when individuals are deceived into clicking on malicious links that transmit harmful code to susceptible websites, reflecting the attack to the user’s browser.
The flaw was discovered on May 8, 2023, and fixed on May 11, 2023, through the release of version 5.7.2. However, on May 14, 2023, a proof-of-concept (PoC) exploit for the vulnerability was published on GitHub, making it easily accessible to attackers.
WordPress has published a page about security hardening that recommends hardening security tasks such as regular database backups, obtaining themes and plugins from trusted sources, and using strong passwords.
WordFence, a security company, has reported millions of attempts to probe and over 6,900 exploitation attempts related to the vulnerable plugin.
According to a recent report by web security company Akamai, hackers actively take advantage of the cross-site scripting (XSS) vulnerability found in the WordPress Advanced Custom Fields plugin. This exploitation occurs as part of a widespread scanning campaign by threat actors.
In the report, web security company Akamai revealed that threat actors have begun exploiting the vulnerability in the Advanced Custom Fields plugin. These attackers actively utilize the sample code released by PatchStack, copying and reusing it for their malicious purposes.
This article emphasizes the importance of patch management and keeping informed about available updates as a crucial part of an organization’s security and risk-reduction strategy.
Users of the Advanced Custom Fields plugin for WordPress are urged to update to version 6.1.6 after discovering a security flaw.
WordPress has published a page about security hardening that recommends hardening security tasks such as regular database backups, obtaining themes and plugins from trusted sources, and using strong passwords.
Download the latest WordPress plugin using this link.
Lastly, ensure the security and integrity of your website by addressing potential impacts from recent WordPress vulnerabilities. If you require assistance with a website audit to determine if your site is affected, feel free to reach out to us without hesitation. Our team of experts is ready to help you assess any vulnerabilities and safeguard your online presence. We are here to help – 888.485.5132, [email protected], contact form.
Sources/Links:
- https://wordpress.org/plugins/advanced-custom-fields/
- https://www.bleepingcomputer.com/news/security/hackers-target-vulnerable-wordpress-elementor-plugin-after-poc-released/
- https://wordpress.org/documentation/article/hardening-wordpress/
- https://thehackernews.com/2023/05/new-vulnerability-in-popular-wordpress.html






Leave A Comment